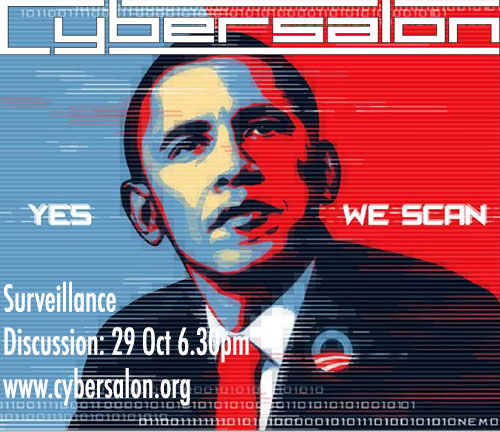
29 October: Total Surveillance
Thanks to Edward Snowden we now know the British state conducts unprecedented interception of data flowing in and out of the UK Internet. It does so without individual warrants. This massive surveillance is widely thought to be lawful and bigger than that of the US. In the US surveillance is conducted with some protections for US citizens. Yet while a debate about surveillance has started in the US, it has so far passed the UK by.
In fact UK citizens are double surveilled. As foreigners for the purpose of US surveillance our use of US cloud based services – like Gmail – make us fair game for warrantless US surveillance as well.
In this Salon we’ll discuss issues like
- “They do it because they can”: What is the role of big data technologies and advances in UX and hardware in the increase in government ability to surveil, and what are the trends – what does the future hold?
- What’s the fuss? Is it ok for Google to know more about us than the government? And – by the way – If you have nothing to hide, then what’s to fear?
- What are the implications for Net freedom around the world, and for the very character of the Internet? Is the Net a commons or as an American general recently claimed, a global free-fire zone?
- If we accept that people are not about to stop using the Internet, what is the best way to counter surveillance? Is the solution to snooping: technological, politics or the market?
Moderator: Wessel van Rensburg, former investigator for the South African Truth and Reconciliation Commission and digital strategist at RAAK.
What is the best way to counter surveillance? Is the solution to snooping: technological, politics or the market?
TICKETS: £5 IN ADVANCE FROM
Running Order
Doors: 6.30pm
Talk: 7.05pm – 8.40pm
Drinks and Mingling: till 9.30pm
9.30pm onwards: Drinks and discussions continue at the Big Chill Bar, Dray Walk (opposite DigitasLBi, pedestrian street off Brick Lane).
Hello,
For tonights cybersalon is it possible to get tickets on the door?
If so how much will they be?
Regards,
N